Infineon’s TPM security chip vulnerability
Applicable models
[TPM spec version: 1.2 firmware version: 4.40] VJZ12A* [TPM spec version: 2.0 firmware version: 5.51] VJZ13B* VJZ131*
Explanation
On October 10, 2017 information disclosure on Infineon’s TPM security chip vulnerability was made.
(www.infineon.com/TPM-update) For TPM firmware that do not support this issue, an RSA key generation algorithm less than expected strength were used. You may be affected if you are using Windows BitLocker Drive Encryption TPM or Virtual Small Card.
This page will guide you on the correspondence of VAIO Corporation towards the vulnerability of TPM security chip.
Please note that Intel PTT-equipped models are not applicable to this issue.
・How to check TPM spec version and firmware version
[How to check from TPM management (Microsoft management console snap-in)]
-
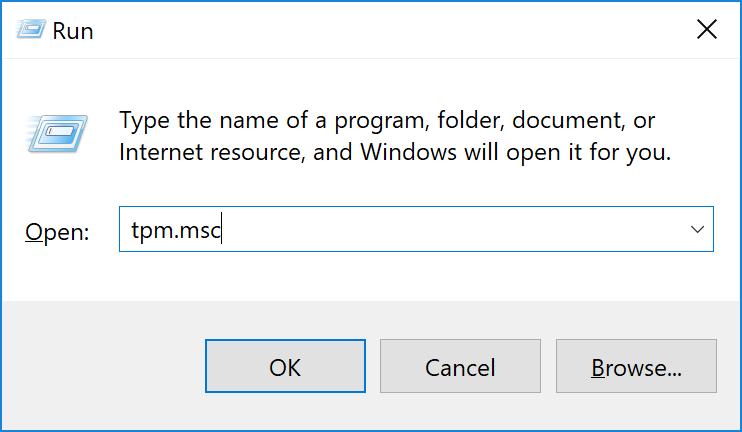
Press [R] key while pressing [Windows] key. Or, go to [Start] menu and click [Run].
-
[Run] dialog will appear, so enter [tpm.msc] and select [OK].
3. [Manage local computer TPM] will boot, so check the [Spec version] and [Manufacturer’s version] under [TPM manufacturer info].
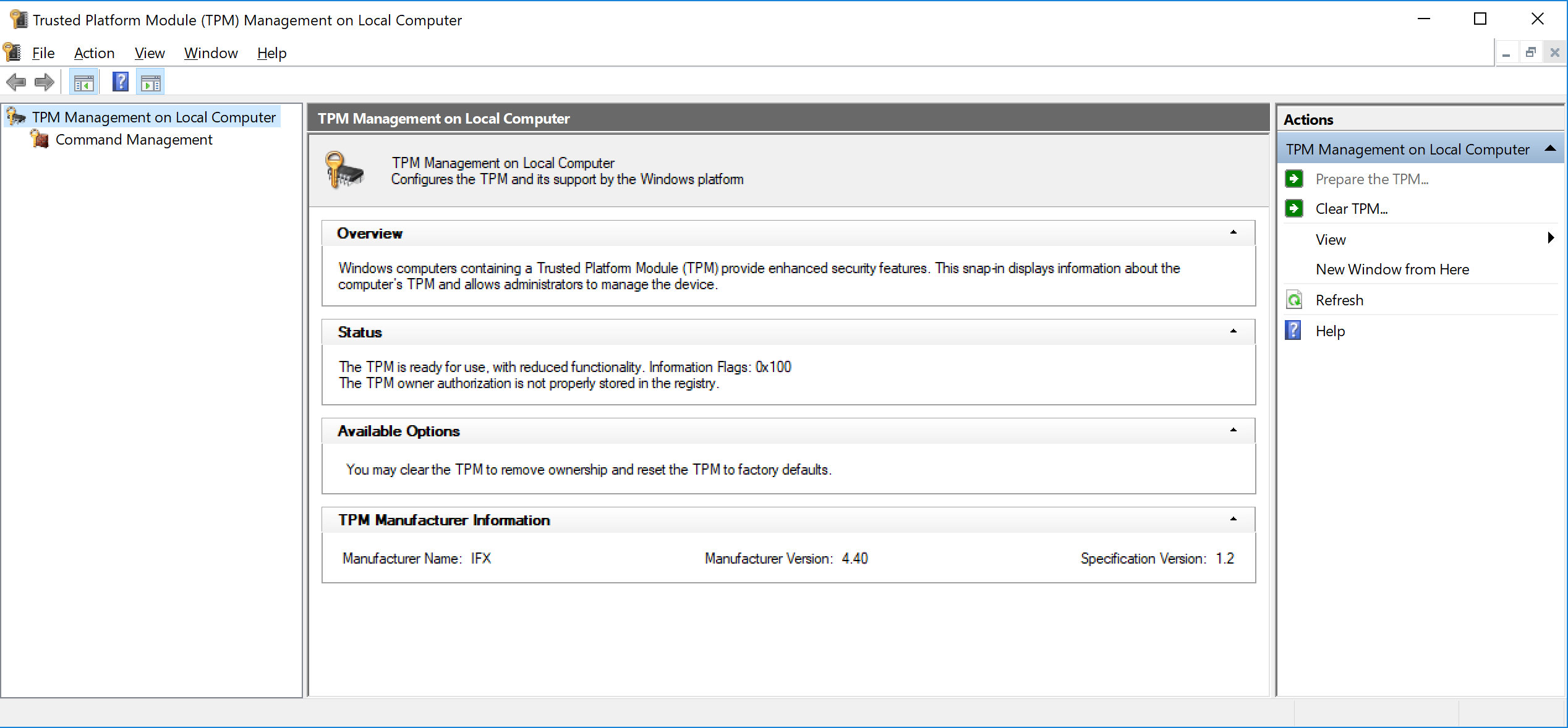
※The screen layout varies depending on factors such as the OS version being used.
TPM firmware version comparison table
| Spec version | Pre-measure firmware versionrun | Post–measure firmware version |
| TPM1.2 | 4.32 | 4.34 or later |
| 4.40 | 4.43 or later | |
| TPM2.0 | 5.00 | 5.62 or later |
| 5.40 | ||
| 5.51 |
How to correspond
[TPM spec version: 1.2] Please click here to down load TPM firmware and run.
[TPM spec version: 2.0] Please apply the latest Windows update program from Windows Update. ※TPM firmware updater is currently under construction. We will make it public as soon as it becomes available. By applying the latest Windows update program, TPM hardware generated RSA key is replaced with software generated RSA key. Please check whether the latest update is applied by the following method: